Mobile devices have become a key part of our daily lives, to the point that many of us openly feel undressed without our phones. As a result, our phones go everywhere with us. However, it’s important to remember that some applications have requested access to our location information. Do all of these apps need to know precisely where we are?
Jackson Thornton Technologies News + Updates
User authentication is a critical security feature for a business, specifically because it helps to minimize a significant threat to your business. This is why we’re so adamant that you should require multi-factor authentication wherever it is available… but is a better way to authenticate your users on the horizon?
We are major advocates for multi-factor authentication, but it’s also important to understand that it’s not a catch-all solution. In fact, it has forced cybercriminals to be even more innovative to find alternative methods of attack. One method hackers use to gain access to your systems is to use what’s called MFA fatigue to their advantage.
There are countless moving parts to any successful business, and smaller companies often have the issue of their employees juggling multiple different tasks and wearing all kinds of different hats in addition to their outlined job duties and responsibilities. You might encounter situations where you don’t know what to do, and it can be overwhelming when so much needs to get done in so little time.
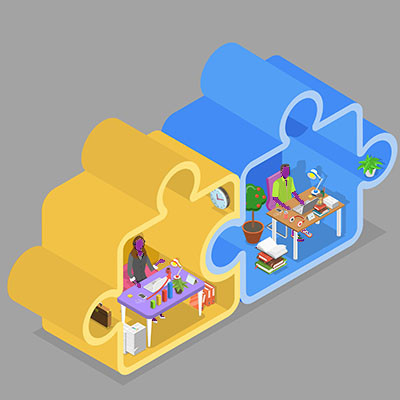
Many businesses, seeking to balance the positives brought by remote work to the value that in-person, face-to-face operations have to offer, have leaned into hybrid work practices. This has led to many reconsidering how their office space is set up. Let’s dive into how these considerations are now shaping the workplace.
Chances are, you’ve gone through some old files and weeded through them, deleting what is no longer needed. This is especially important when you are upgrading your storage and getting rid of your existing storage media or an old computer. Let’s talk about what really happens when you’re doing so—chances are, you may be overlooking a serious security issue.
Okay, let’s say you’ve been infected by a ransomware attack, and (against our advice) you’ve elected to pay the ransom. That’s the biggest cost that comes with it, right?
Unfortunately, wrong. A ransomware attack comes with a lot more financial impact than just the payment the attacker demands. Let’s go over some of these other costs that can actually outpace that of the ransom.
There is always the possibility that you have been involved with a data breach and you simply have not been contacted by the affected party. Plus, if a hacker has managed to crack a website or service without being detected, you wouldn’t be notified in any case, either. Ask yourself this question: if I were to be involved with a data breach, how would I know it, and what can I do about it? And what is my data being used for anyway?
When it comes to drives for your computer or workstation, you have a couple of options available to you, one of which is the solid state drive, or SSD. What’s the difference between your typical hard drive and an SSD, you ask? Well, today we’ll find out. We’ll break down some of the details about SSDs, including how they are different from your traditional hard disk drive, and why you might consider implementing one.
You might be surprised by some of the security breaches and vulnerabilities out there, including some for apps that you would never suspect, like Windows’ Calculator application. Hackers are always looking for new ways to infect endpoints, and nothing exemplifies this better than this particular threat, one which utilizes the Windows 7 calculator app to launch attacks against Microsoft operating systems.
Every business depends on productivity, but there are many different forms that productivity can take. The types that every business prefers are the actions that result in improved revenue generation. That’s not to say that all work that is done for your business isn’t important, but the more that can be done to make money, the better off your business will be. Let’s take a look at three ways your business can shift the way they do things with the use of technology.
The Internet of Things can be a tricky concept to wrap your head around, and it certainly doesn’t help that so many new smart devices are being added to it day-in and day-out. Let’s take a look at what makes up the Internet of Things and why it’s important to know what it is from a business perspective.
Let’s begin by making one thing abundantly clear—all businesses and industries could potentially be targeted by ransomware, regardless of their size or target audience. However, as of late, some industries have been targeted more and more. Let’s examine some of the commonly targeted industries that ransomware is frequently waged against.
Let me ask you a question: is there anything in your office that doesn’t rely on technology in some way, shape, or form (and no, the old coffeepot that makes the perfect cup doesn’t count)? Increasingly, the answer to that question is “no.” Let’s review how much the average business nowadays relies on IT to really reinforce how ubiquitous technology has become.
Let me ask you a few questions—first, how confident are you that you could spot an online ruse, and second, did you know there’s a stain on your shirt right now?
Did you look?
If so, you’ve just fallen for the school playground version of social engineering, a serious threat. Let’s discuss the kind that you’re more likely to see in terms of your business’ cybersecurity.
As a business professional, it’s your responsibility to protect your company’s digital assets from cybercrime, but the path forward is not always so easy or clear-cut. Without a thorough knowledge and expertise of IT security at your disposal, it can be challenging to protect your infrastructure as adequately as it needs to be. Here are some of the common issues that involve cybersecurity, as well as how you can address them.
The past few years have made many people understandably antsy about their health and spending extended amounts of time around other people—which can make coming into the office a very, very stressful experience for some. How can you make your office a healthier place so your team can feel a little more secure as they work?
Your business is your livelihood, so it only makes sense to invest in its protections so that your livelihood is secure. This will require a strategic approach. Let’s go over what your business needs to remain sufficiently secure, and what you should look for from each to get the best, most secure option.